
Multi-factor authentication is not enabled for users at your client, but now you are being asked the following question:
Is there not a way to protect users in the event that some have used the organization’s 365 username and password to access non-Microsoft sites which could be compromised?
You can tell them that yes there is a way to solve this situation. The solution is to use Conditional Access policies.
These days bad actors obtain lists containing usernames and passwords from sites that have suffered security breaches. These lists are used, from different countries, to attempt to access the organization’s resources.
The best solution would be to enable multi-factor authentication.
“With strong multi-factor authentication (MFA) in Azure Active Directory (Azure AD), protect your organization from breaches related to lost or stolen credentials.”1
However, it may not be possible to enable multi-factor authentication for various reasons.
It is possible to only allow access to organizational resources from targeted locations by means of “Using the location condition in a Conditional Access policy” available in Azure Active Directory now called Microsoft Entra ID.
To meet the customer’s needs, the Conditional Access policy should allow the users in question to only access organization resources from a named location.
A named location can be defined as follows in the following scenarios:
Here are the necessary conditions to be able to achieve the proposed solution:
Access the Microsoft 365 admin center in the client’s tenant.
Then proceed to the Identity admin center.
You are now in the Microsoft Entra admin center.
To access the Conditional access section, go to Protection
Then to Conditional access
You are now in the conditional access management screen.
As stated earlier, for the proposed solution to be feasible, the Conditional Access policy must target the users in question and allow them to only access the organization’s resources from the named location(s) and no other.
This is based on the following scenario which was discussed before:
Let’s start with named locations.
Simply go to the named locations management window to be able to create a named location that will be the one from which access will be allowed.
By clicking on Named locations, in the conditional access management window, the location in question can be created.
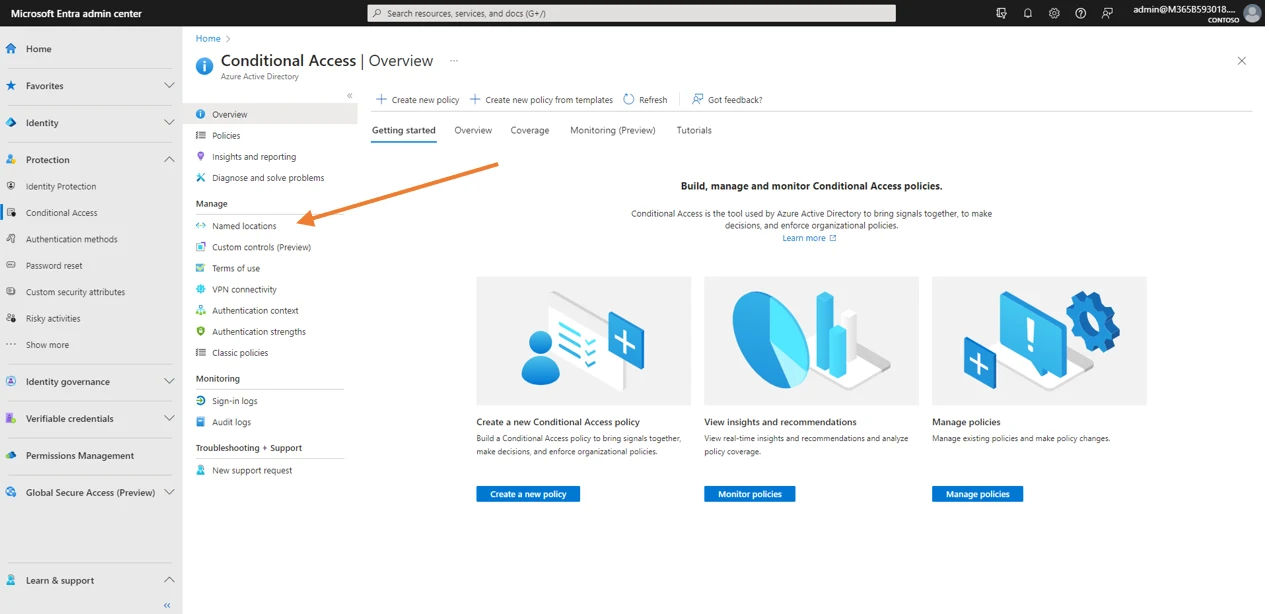
Once in the Named locations management screen, click on Countries location.
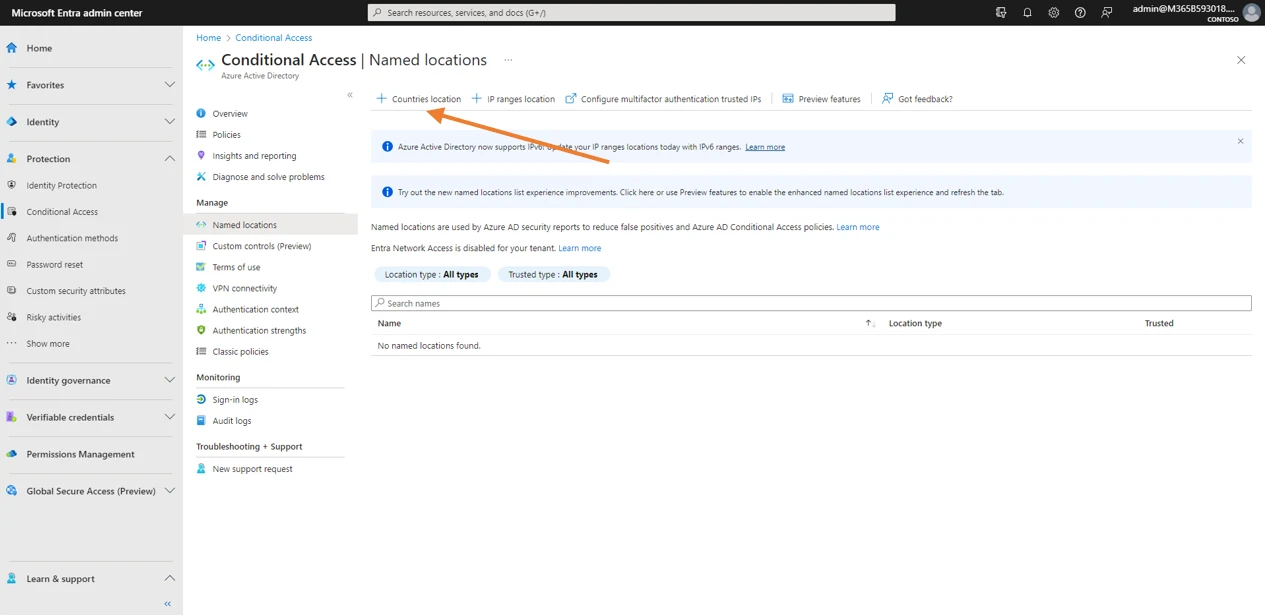
This will open the configuration window.
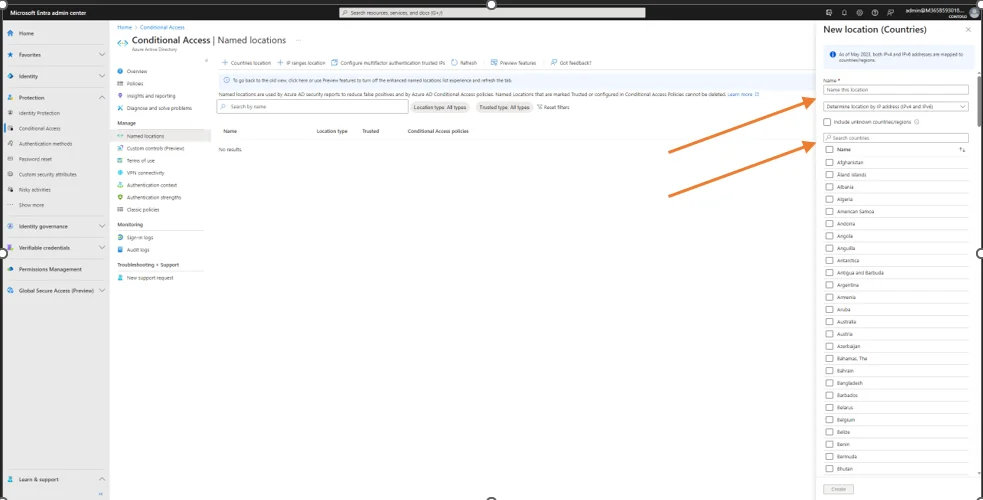
Start by giving a name to the location, in our example this name is ‟Canada”. Then click on the search window and type Canada.
Then click on Canada and finally on create.
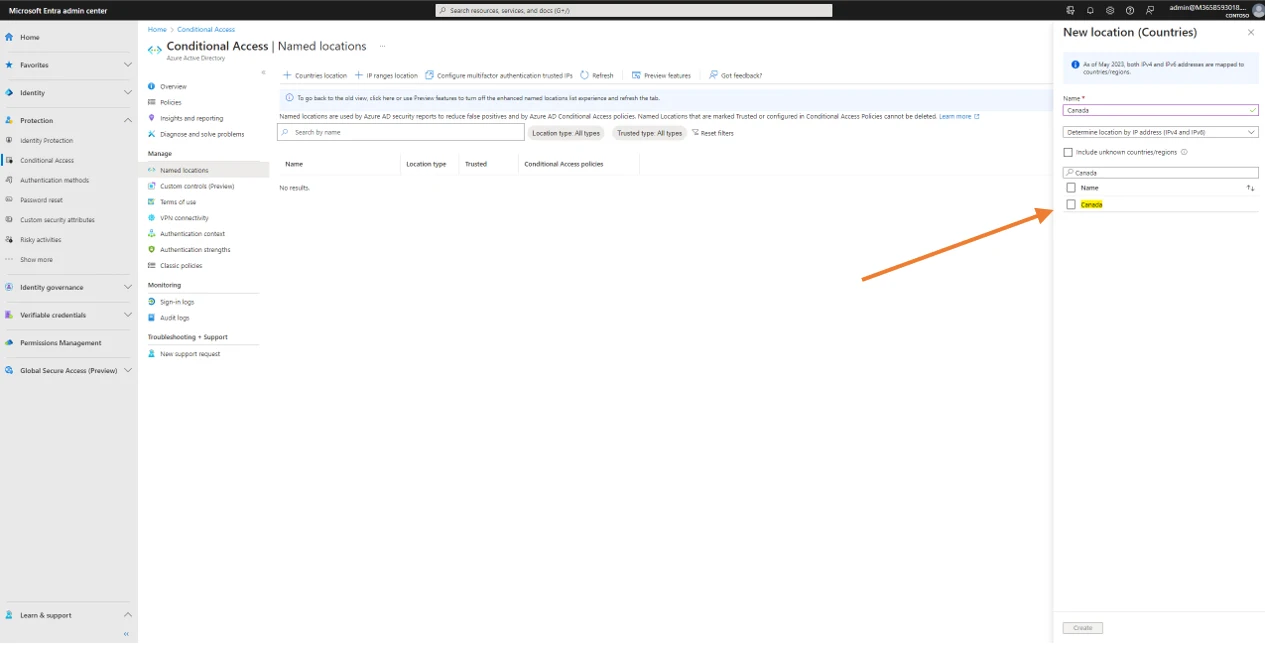
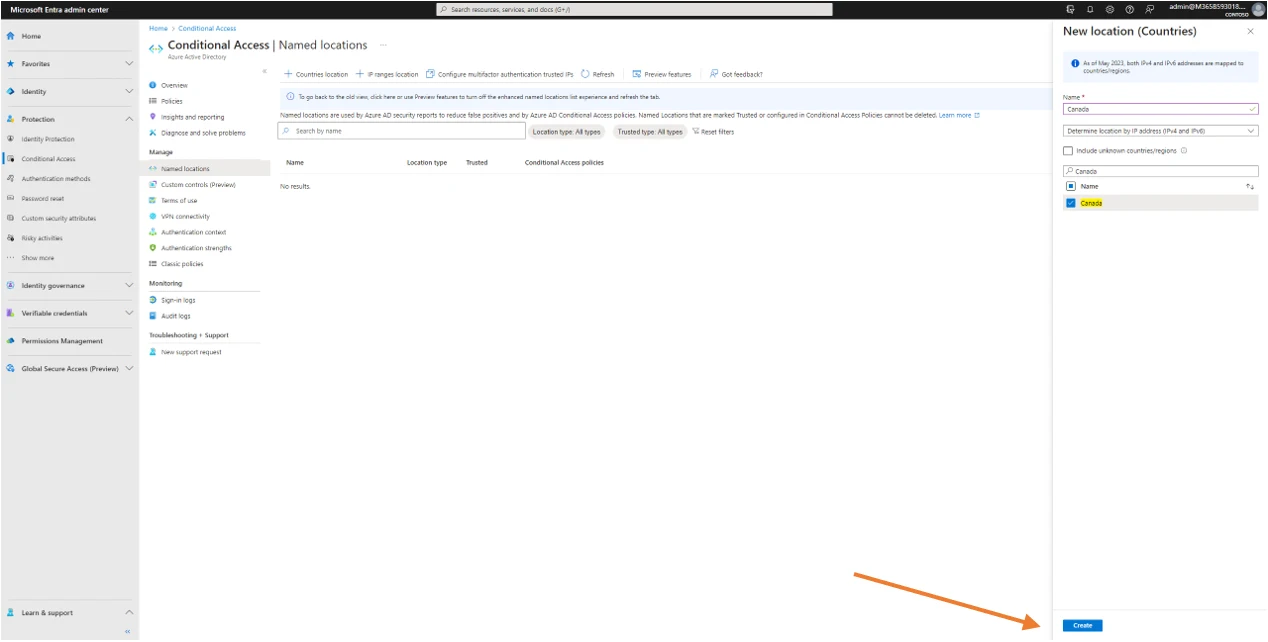
Which gives this result.
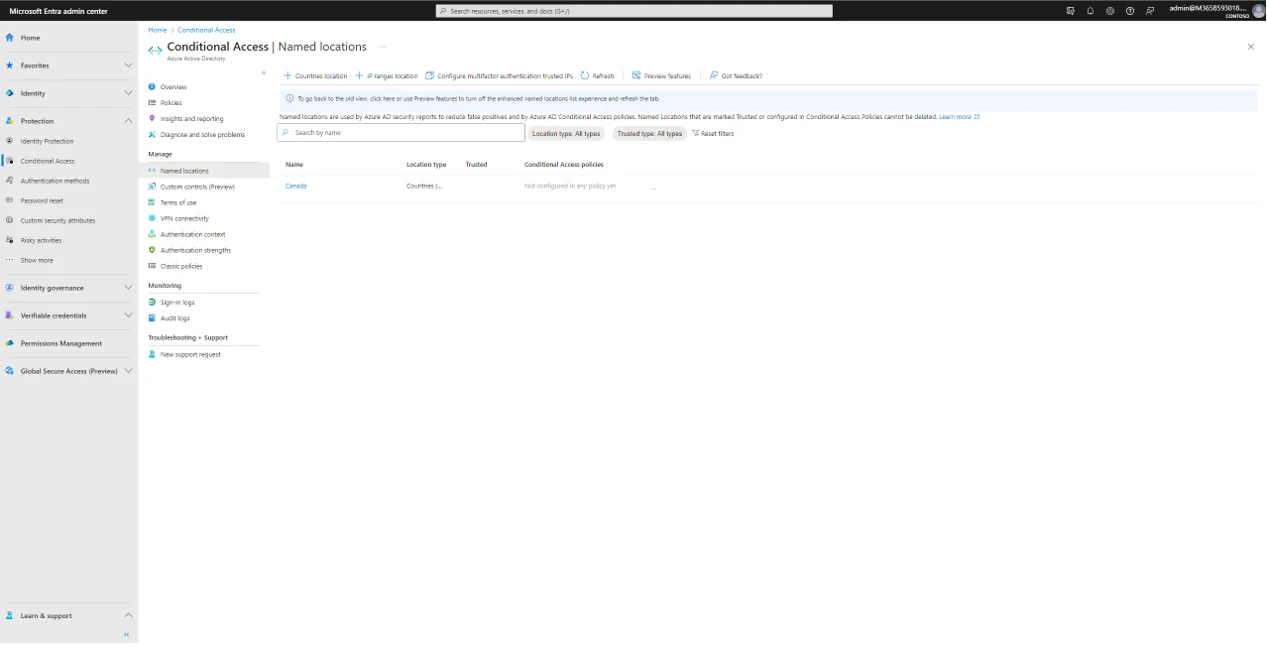
Now create a conditional access policy “only from Canada”.
Click on Policies
Then new policy
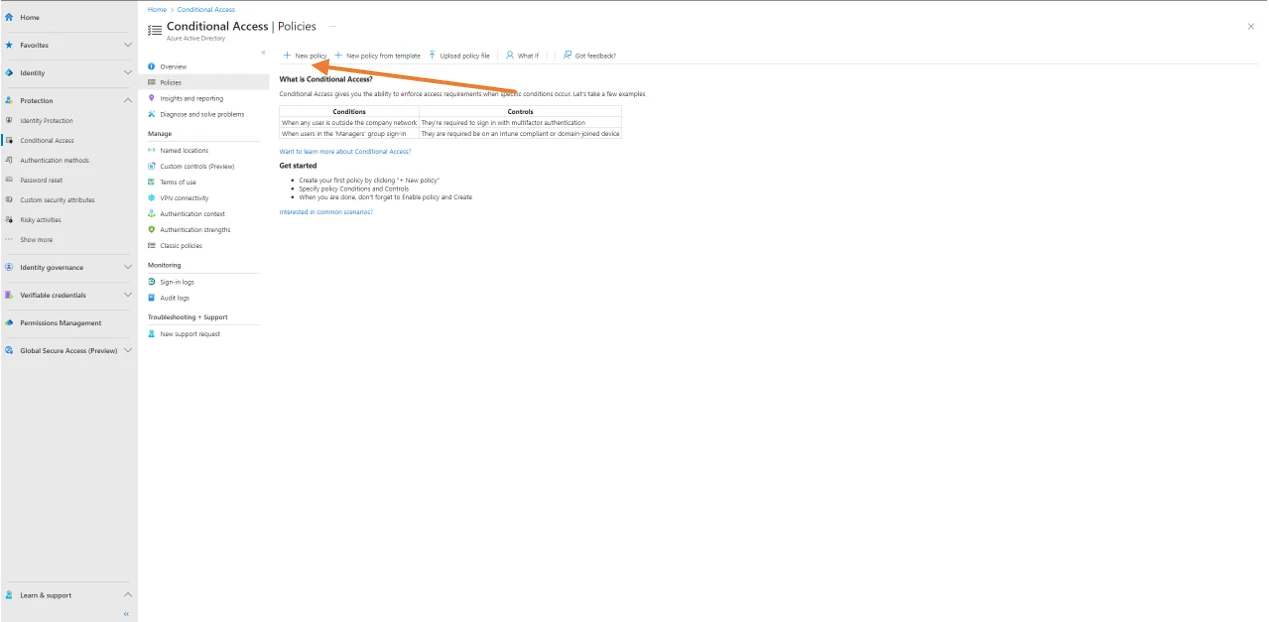
In this conditional access policy management window, the following sections are the ones that interest us to achieve the expected result.
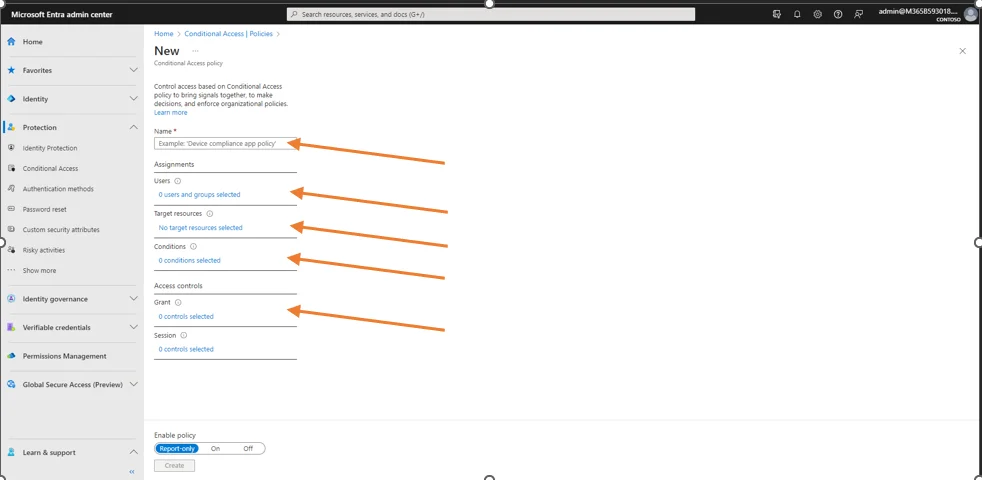
In the example, for the first part of the configuration, add the name “only from Canada” as the policy name.
Second, navigate to the Assignments section, in the Users subsection click on all users. In the example all users have been chosen as those targeted by this policy.
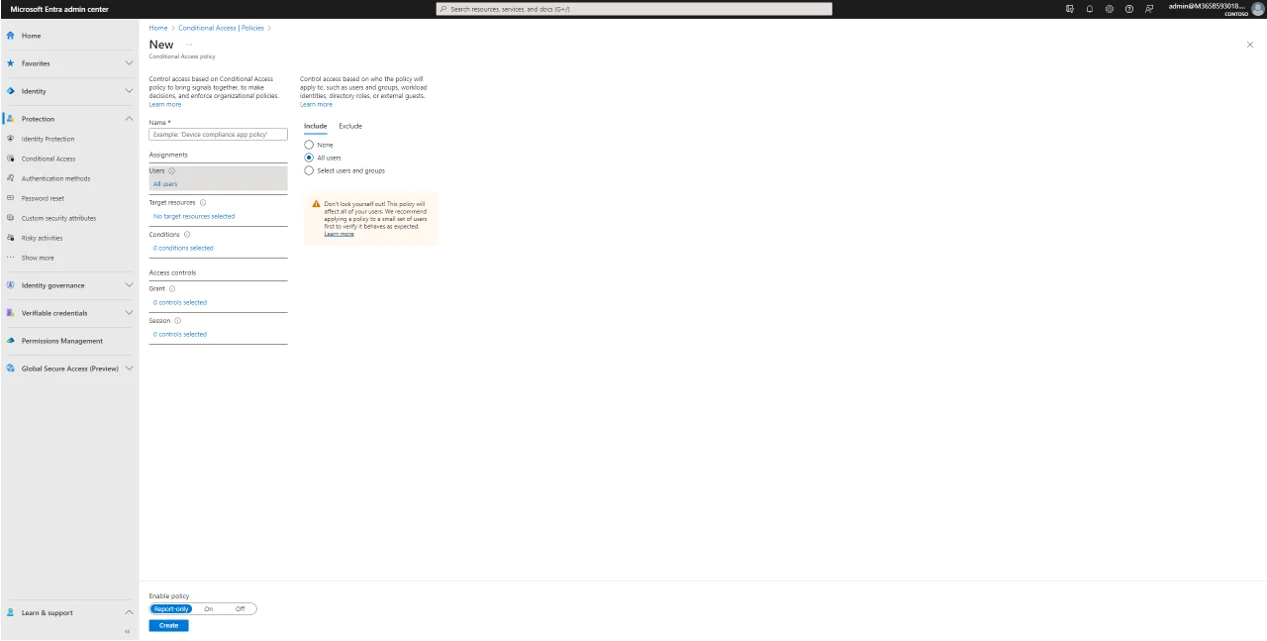
Third, navigate to the Target Resources subsection. Include All cloud apps. No apps are excluded from this policy.
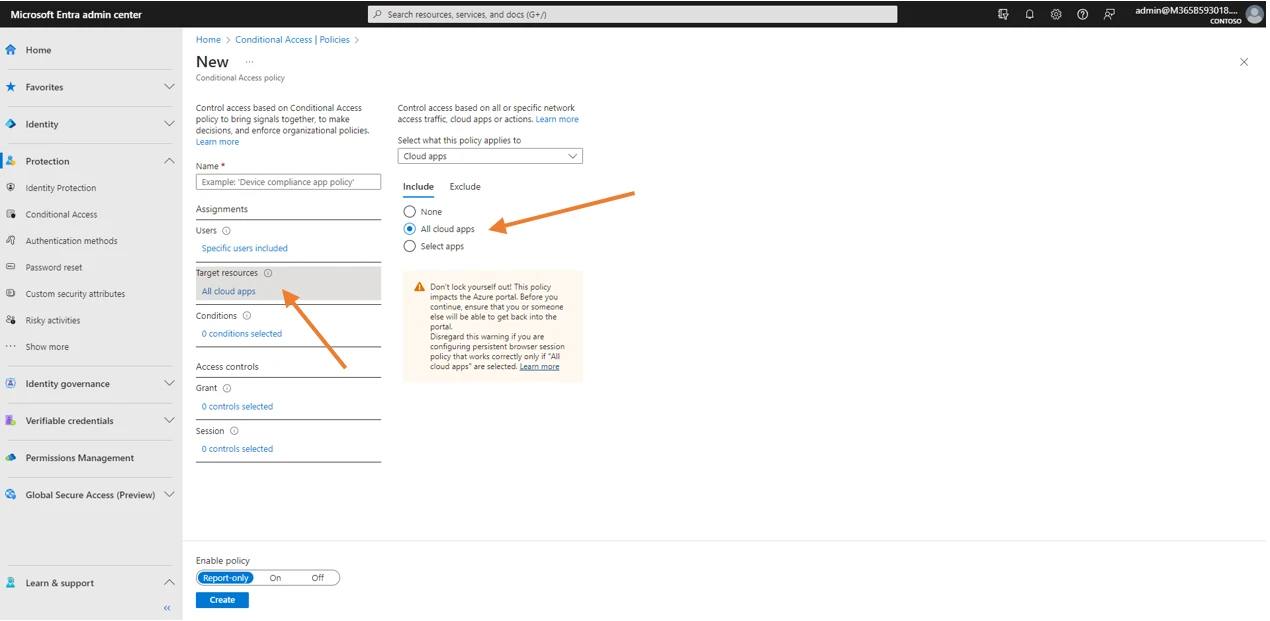
Fourth, navigate to the Conditions subsection, click on 0 conditions selected, then in Locations click on Any location, under configure choose yes and choose Any Locations
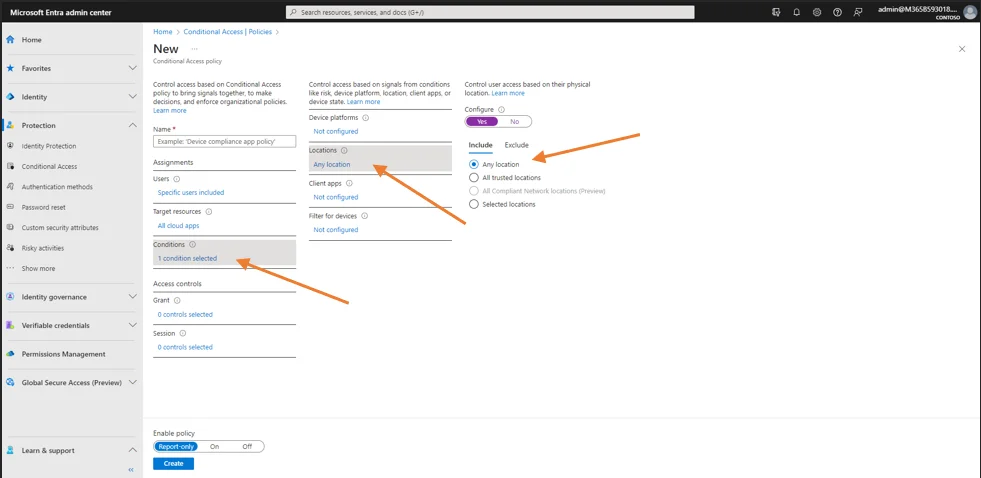
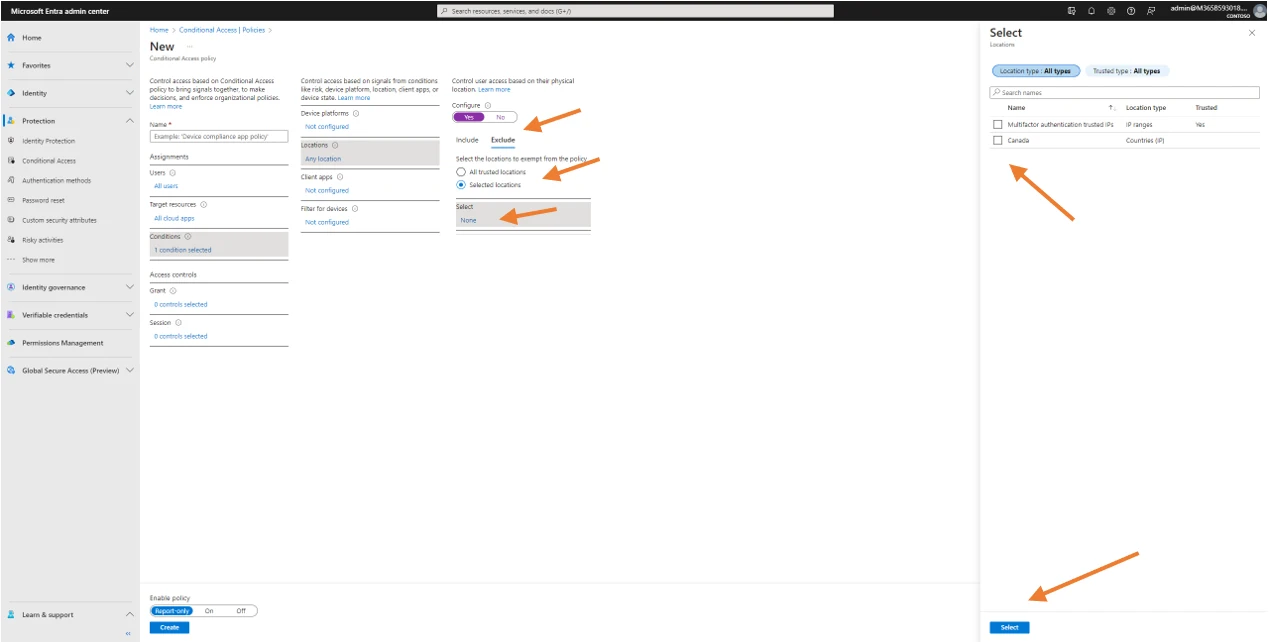
Then, click on Exclude, Selected locations, none and check the desired location and click Select.
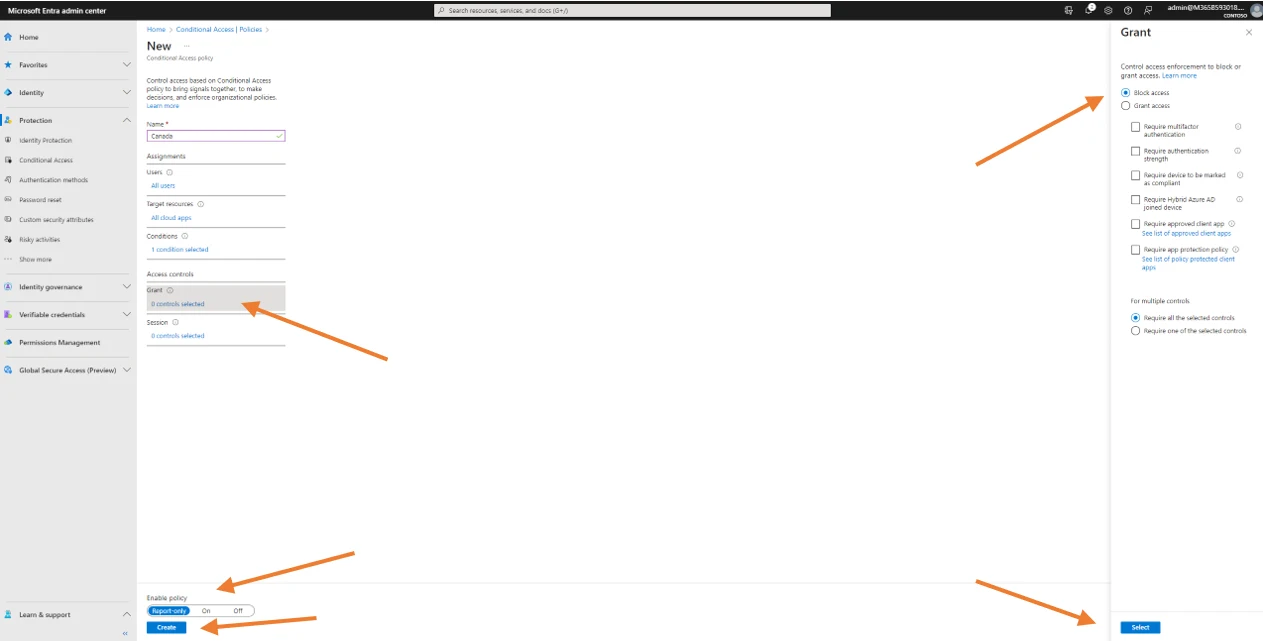
Finally, as far as the configuration requirements, navigate to the Access Control section and in the Grant subsection click 0 controls selected. Then click on Block access and finally on Select.
You will see the following message:
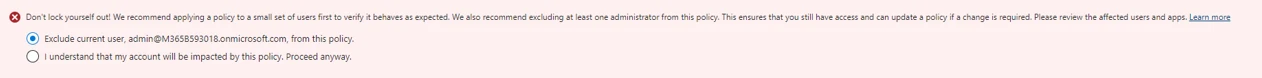
It is up to you, whether or not, you follow the recommendation to exclude at least one administrator.
Then choose the enabled mode and click on create. This is the result.
As the example was able to demonstrate, in this situation, the use of conditional access strategies makes it possible to address certain shortcomings when you cannot activate multi-factor authentication.
The example that was used deals with the two scenarios listed:
The approach being to restrict the scope of those who attempt to gain access to the resources.
The functionality discussed in this article is included in Microsoft 365 Business Premium.
Feel free to contact our experts at ITCloud.ca if you need help to ensure that your customer data is secure.
Email us now at partners@itcloud.ca
1 – Multifactor Authentication (MFA) | Microsoft Security
2 – Using networks and countries/regions in Azure Active Directory – Microsoft Entra | Microsoft Learn
3 – Azure Active Directory – Microsoft Entra | Microsoft Security
4 – Using networks and countries/regions in Azure Active Directory – Microsoft Entra | Microsoft Learn